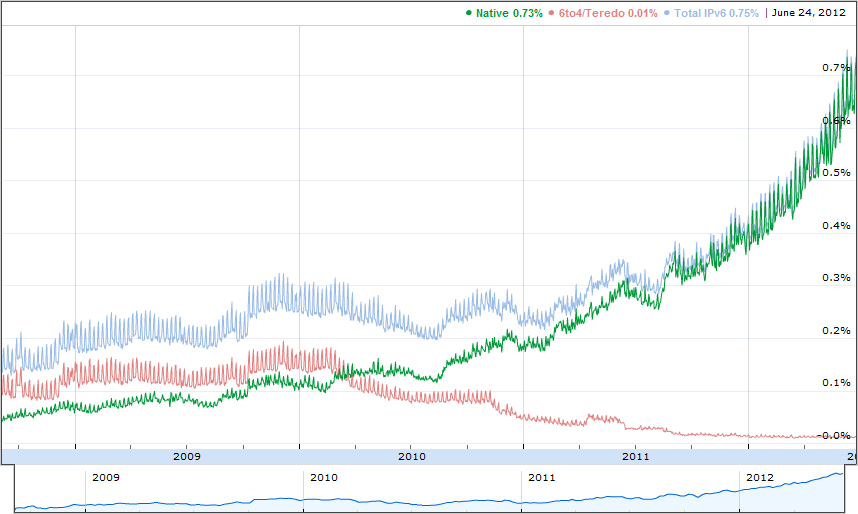
Check out a round-up of apps that will let you do less and benefit more from your social media marketing efforts.
It's safe to assume that anyone who has a substantial number of Twitter followers (say, tens or hundreds of thousands) is not only interesting and entertaining... but is also really good at managing the process.
If you want to be good at managing your own Twitter process the problem is there are hundreds of Twitter tools and apps, including some really good tools you probably aren't using.
So I conducted a totally unscientific survey: I asked some of my Twitter followers who have at least 5-digit followings which tool they use the most for managing Twitter.
The clear winner was Buffer, a tool that lets you schedule tweets so you can avoid joining the tweet-a-minute club and so you connect with followers when they're most likely to be available and active.
If Buffer works for the big boys and girls, it can work for me and you, so I asked Leo Widrich, Buffer co-founder, for ways to streamline your Twitter efforts by leveraging Buffer:
Turn Twitter and Facebook into a social media dashboard.
Install a Buffer browser extension and you can turn your Twitter feed and Facebook stream into a social media dashboard.
Buffer buttons will appear wherever you need them, including the tweet and retweet buttons and the Facebook share button. The extension also reshares an actual image from Facebook photos.
Sharing content is a lot easier if you can share as you go; the extensions also work with Google Reader, Reddit, and HackerNews.
For more, here's Buffer's guide to using browser extensions.
Create Power Tweets.
With Twylah you can create personal brand pages for tweets.
Twylah also allows you to send what they call Power Tweets, making a tweet look like a small blog post. According to Twylah, Power Tweet pages increase clicks and engagement time (time spent with content) by a factor of 40, since Power Tweets are surrounded by short snippets of text and other relevant content on the Power Tweet page.
For more, here's Buffer's guide to Power Tweets.
Become a content curator.
Want to curate content for Twitter followers and Facebook fans? Check out Mr. Reader, an iPad RSS reading app. Mr. Reader lets you pull from your Google Reader feeds and browse using a very slick app. Then you can Buffer directly from Mr. Reader and post to different social networks and accounts.
If you've gotten away from RSS feeds, Mr. Reader might be the reason to go back.
For more, here's Buffer's guide to sharing from Mr. Reader.
Save and share.
Read It Later, now called Pocket, lets you save articles, videos, etc and--you guessed it--read it later.
Now you can also Buffer anything you save in Pocket, allowing you to read later and share from one place.
Create data-driven tweet schedules.
Tweriod is arguably the best Twitter analytic tool, especially where determining the best times to tweet is concerned. Twitter analyzes past tweet performance, when followers are online and engaged... and keeps automation tools from skewing results.
Integrate Buffer into Tweriod and it will suggest optimal Buffer timing and help you create data-driven schedules.
For more, here's Buffer's guide to integrating Tweriod.
Do you have Twitter tools and apps you love? If so, share them in the Comments below.